Home > Blog > Artificial Intelligence
Subscribe to Our Blog
Get the latest trends, solutions, and insights into the event-driven future every week.
Thanks for subscribing.
You can’t spell “agentic” without “agent”, and hence this blog post is dedicated to the anatomy of agents in agentic systems. In simple terms, you can think of an agent as an LLM-enabled microservice that receives instructions to perform a specific goal. In Solace Agent Mesh, an agent is the main processing unit that receives prompts, executes a couple of LLM-supported actions, and gives the response back to the original requestor.
But what exactly are the building blocks of an agent in the context of Agent Mesh? This blog post will delve deeper into the anatomy of an agent to see what it’s actually made of. Spoiler alert: it’s not just Python code 👀
Configuration-First Philosophy
Solace Agent Mesh takes a configuration approach for the components, meaning that you need to define the behavior of the component in YAML files. Yes, you heard it right, its the great markup YAML that sends you down a philosophical debate of tabs vs spaces. But fear not! Once you understand the structure, it’s actually quite elegant. This configuration-first approach means you can modify agent behavior without diving into code (most of the time), and provides several advantages, including maintainability, version control integration, and environment-specific customization to reduce deployment complexity.
Dissecting the Agent: The YAML Anatomy
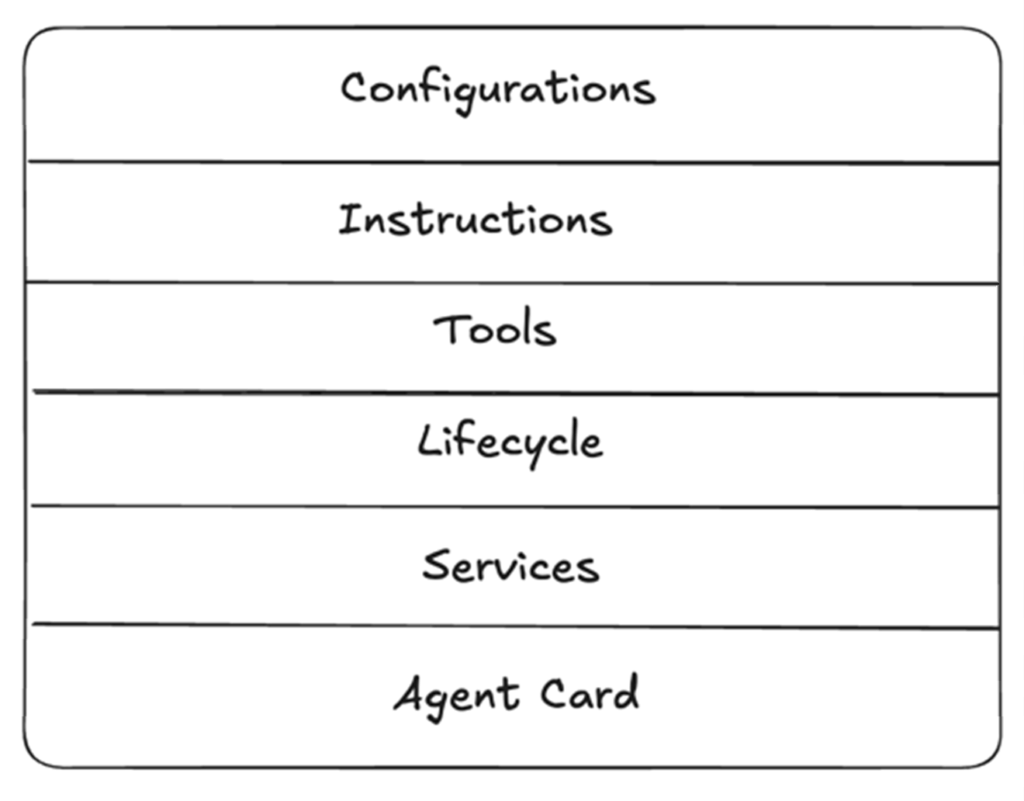
Let’s break down the anatomy of an agent YAML file, examining each component that contributes to the agent’s functionality:
Configurations – Agent Identity and Core Settings
This section includes system-level configurations for agents, including the agent’s identity and model configurations. These settings establish the agent’s unique identity within the mesh and define its operational parameters.
# Basic agent identity
namespace: ${NAMESPACE}
supports_streaming: true
agent_name: "WeatherAgent"
display_name: "Weather Information Agent"
# LLM model configuration
model: *general_model
Note that the namespace provides unique identification for the agent within the mesh, preventing naming conflicts and enabling proper routing. This is one of the places where the true powers of Agent Mesh being built on event-driven architecture and pub/sub fundamentals shine. The agent_name and display_name provide both programmatic and human-readable identifiers for the agent within the system.
Instructions – The Agent’s System Prompt
This is the natural language description of the agent’s purpose that gets passed to the LLM. This system prompt defines the agent’s behavior, capabilities, and operational guidelines.
instruction: | You are a Weather Information Agent that provides accurate weather data and forecasts. Your purpose is to help users obtain reliable weather information. You can: 1. Retrieve current weather conditions for any location 2. Provide detailed weather forecasts 3. Offer weather-related analysis and insights Always prioritize accuracy and provide comprehensive information based on available data.
The instruction field serves as the agent’s behavioral foundation, defining its role, capabilities, and response patterns. Clear, specific instructions ensure consistent and predictable agent behavior across different interaction scenarios.
Tools – The Agent’s Capability Framework
This is the critical section that defines the capabilities of the agent. Tools represent the actual functions your agent can execute. There are three different categories of tools in Solace Agent Mesh:
- Built-in Tools: These are pre-developed functionalities that can be readily integrated into agents, providing standard capabilities without custom development. Built-in tools provide standardized functionality for common operations such as file management, data analysis, and system integration. These tools are maintained as part of the platform and offer reliable, tested functionality. Note that built-in tools can also be packaged into built-in groups to be imported as a bundle
- Custom Tools: Domain-Specific Implementation. These are Python modules that you develop to implement custom behavior specific to your use case and business requirements. Custom tools enable the implementation of specialized functionality tailored to specific business logic or integration requirements. These tools provide maximum flexibility for unique operational needs. Tools could also be used to invoke agents in other systems such as AWS Bedrock, SAP Joules, and Salesforce Agentforce agents. Note that Solace Agent Mesh has support for a plugins ecosystem which allows porting tools as packaged Python modules that can be installed using various package managers to extend the functionality of Agent Mesh in a modular, shareable, and reusable way
- External Server Tools: These are tools provided by 3rd party external implementation such as MCP servers, A2A servers, and other external services, enabling integration with existing infrastructure and third-party systems.
The power of normalizing tools in Solace Agent Mesh lies in the ability to combine different categories of tools within a single agent, enabling comprehensive functionality through modular composition. For example, you can have an MCP based agent and extend it with built-in tools along with custom python tools to bundle it in one agent.
Lifecycle – Resource Management
This optional configuration handles resource management during the agent’s operational lifetime, including initialization and cleanup procedures. Proper lifecycle management ensures efficient resource utilization and system stability. Lifecycle functions provide hooks for resource initialization and cleanup, ensuring proper system resource management throughout the agent’s operational cycle.
Framework Services – Core solace agent mesh infrastructure access
These are built-in capabilities for accessing Agent Mesh core services including session management, artifact access, and system logging. Framework services provide essential infrastructure capabilities. Framework services enable agents to access platform-level functionality such as persistent storage, session management, and logging infrastructure, providing a consistent operational environment.
Agent Card – Capability Specification
This is an A2A compliant specification that includes metadata describing the agent’s capabilities, skills, and system visibility. The Agent Card serves as the agent’s public interface specification. The Agent Card enables agent discovery and interoperability within the mesh. Each skill corresponds to actual agent capabilities, providing accurate capability advertising for system integration.
# Agent card (describes the agent's capabilities)
agent_card:
description: "A comprehensive weather agent providing current conditions and forecasts"
defaultInputModes: ["text"]
defaultOutputModes: ["text", "file"]
skills:
- id: "weather_lookup"
name: "Current Weather Lookup"
description: "Retrieves current weather conditions for specified locations"
- id: "weather_forecast"
name: "Weather Forecasting"
description: "Provides weather forecasts for specified locations and timeframes"
- id: "file_operations"
name: "File Operations"
description: "Create, read, and manage weather-related files and artifacts"
Final Thoughts
Solace Agent Mesh provides several key advantages through its modular design Tool composability allows you to combine built-in tools with custom Python functions and external MCP servers within a single agent, creating comprehensive functionality from diverse sources. Component reusability enables you to configure the same tool function multiple times with different parameters for varied use cases, maximizing code efficiency and reducing development overhead.
Independent development capabilities mean you can develop and test tools, lifecycle functions, and configurations separately, enabling parallel development workflows and easier debugging. Dynamic discovery functionality allows agents to discover and communicate with each other through standardized Agent Cards, facilitating automatic service integration and mesh-wide collaboration. And finally, configuration-driven operations enable you to modify behavior through configuration changes rather than code deployment, reducing operational complexity and deployment risks.
Understanding the anatomy of agents in Solace Agent Mesh provides the foundation for building effective agentic systems. Each component serves a specific architectural purpose within the overall system design. These components work together to create intelligent, capable agents that can operate independently or collaborate within the Agent Mesh ecosystem. The modular architecture enables scalable, maintainable agent development while providing the flexibility to address diverse operational requirements.
That’s it for now. Tune in for the next blog to dive deeper into MCP configurations for agents, where we’ll explore advanced integration patterns for external tool servers.
Explore other posts from category: Artificial Intelligence

Tamimi enjoys educating people about and exploring innovative ways of integrating Solace technologies with emerging tools, technologies and techniques. With this focus in mind he’s helped Solace’s developer relations team run scores of virtual events for individual developers and partners alike, frequently presenting or facilitating tutorials and hands-on workshops.
Prior to Solace, Tamimi played a role at Qlik, a leading provider of business intelligence and data analytics solutions, and was an automation specialist for You.i TV which provides a platform for video streaming apps. His experience in those fields, combined with his event-driven architecture expertise, makes Tamimi highly sought after as a guest speaker on podcasts and – before COVID and hopefully soon again – in-person speaking engagements.
Tamimi enjoys all things tech, and has been actively supporting social entrepreneurship in the Ottawa-area tech community for over a decade. He currently serves as director of a non-profit called Connected Canadians that aims to reduce isolation amongst older adults by promoting digital literacy skills and providing technology training and support.
Tamimi holds a bachelor’s degree in communication engineering from Carleton University, and when he’s not immersed in technology he enjoys photography and DJing.


Subscribe to Our Blog
Get the latest trends, solutions, and insights into the event-driven future every week.
Thanks for subscribing.