by Preena Patel
Modern businesses are rapidly adopting cloud-based computing platforms such as IaaS, PaaS, and SaaS. The dynamic nature of infrastructure management, especially when increasing applications and services, can cause several problems even when organizations adequately resource their departments. These as-a-service models allow organizations to outsource many of the time-consuming IT-related tasks.
As businesses migrate to the cloud, it has become crucial to understand the security requirements for protecting data. Although the management of this infrastructure may be transferred to a third-party cloud computing service provider, the company is ultimately accountable for the security of the data assets.
Cloud service providers strive to ensure the integrity of their servers by implementing policies, procedures and tools in the areas of authentication, authorization and encryption, and enterprises must consider their particular circumstances while securing data, applications, and workloads that are housed on the cloud.
Security problems have grown as the digital environment continues to expand. These hazards primarily target cloud computing suppliers because an organization’s overall lack of visibility in data access and mobility makes them difficult to manage. Regardless of where client information is stored, organizations may experience major governance and compliance difficulties if they don’t take proactive steps to improve their cloud security.
That’s why cloud security needs to be a major talking point for companies of all sizes. Almost every aspect of contemporary computing is supported by cloud infrastructure, across all verticals and all sectors. However, putting in place sufficient defenses against contemporary cyberattacks is essential for successful cloud adoption. Cloud security solutions and best practices are essential for maintaining business continuity regardless of whether a firm uses a public, private, or hybrid cloud environment.
What Exactly is Cloud Security?
Cloud security is a set of practices and tools designed to protect data stored in cloud computing environment from theft, deletion and leakage. Cloud security is required as organizations implement their digital transformation strategy and integrate cloud-based tools and services into their infrastructure. Protective methods include:
- Access control
- Firewalls
- Penetration testing
- Obfuscation
- Virtual private networks (VPNs)
- Not using public internet connections
- Tokenization
The terms “digital transformation” and “cloud migration” have become commonplace in business contexts in recent years. Both expressions are driven by a desire for change, even if their meanings differ depending on the organization.
New challenges in balancing security and productivity levels emerge as companies implement these ideas and work to improve their operational strategy. While moving to a cloud-based environment can have various consequences if done incorrectly, more modern technologies allow firms to develop capabilities outside the confines of on-premises infrastructure. To strike the right balance, it is important to comprehend how modern enterprises may profit from the utilization of connected cloud technology while putting the best cloud security practices into place.
Solace Cloud: What is it?
As I started using Solace Cloud, I could see how well it combines best practices, knowledge, and technology for event-driven architecture (EDA) on a single platform. It is a full event streaming, event management, and monitoring platform. As a software-as-a-service (SaaS), the platform:
- Provided me with everything I needed to hasten the implementation of EDA in my company and to meet the requirements of contemporary use cases that call for real-time, intelligent event streaming.
- Enabled me to build, install, manage, monitor, and regulate my event streaming infrastructure (including the events that flow over it) in the most secure way possible using a simple, unified interface.
I find Solace Cloud to be quite secure. Every level of the platform is developed with enterprise-grade security to keep the event-driven architecture and its data secure.
While Solace completed some deployment tasks for me, most of them I completed myself. In addition, I have come across several deployment options that reference Solace – or customer-owned resources or infrastructure.
Solace Cloud Security Capabilities
Cloud Security Architecture
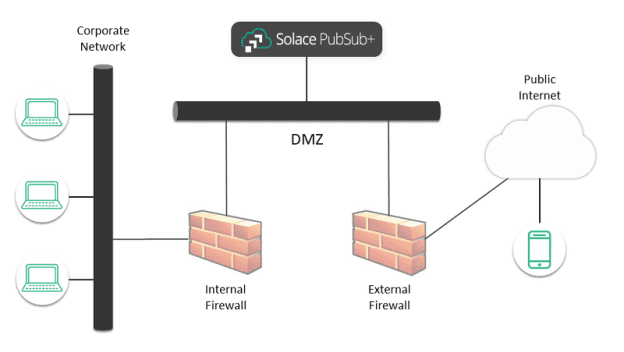
With Solace Cloud, I got the option of deploying our services to public regions, dedicated regions, or customer-controlled regions. Its customer-specific event broker services (non-shared) were deployed in a shared region using public regions and dedicated regions. I used the public Internet to connect applications.
Event broker services are deployed in a region dedicated to each customer, which was ideal for my use case as it required isolated infrastructure and applications that connect via a private network rather than the public Internet.
A customer-controlled region enabled me to deploy to a Kubernetes cluster in a region that I manage. I tuned and started managing the infrastructure and Kubernetes cluster.
The deployment option chosen determines whether the customer manages the security aspects of Solace. My security responsibilities grew as I progressed from public regions to dedicated regions to customer-controlled regions.
Data Security
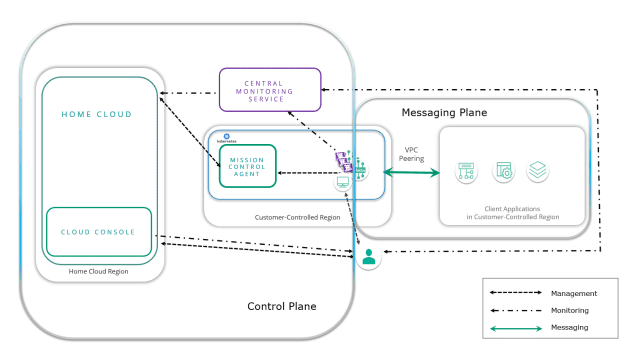
Lots of different kinds of data get distributed by Solace Cloud, including management, monitoring and communication. I find it crucial to understand that the paths taken by the management, monitoring, and messaging data are distinct and clearly defined is critical.
Logically, the control plane (for management and monitoring data) and the messaging plane (for actual communications and interactions) are the two data planes that make up Solace Cloud (for messaging data). This helped me more easily handle both kinds, simultaneously. While stationary or in transit, all my data, including management and messaging data, is secure and encrypted.
Isolation of VPCs and VNets
I chose to deploy the event brokers into a dedicated and isolated VPC. This isolated VPC/VNet provided added security meeting my requirements:
- The event broker must not be accessible via the public internet.
- The event broker needs to run in a secluded environment. (i.e. I didn’t want the event brokers to run into a multi-tenant environment or on a shared public infrastructure).
- I had data localization requirements (I needed a VPC/VNet kept in a specific region of the world).
Authentication and Authorization of Client Applications
To me, it’s amazing to have precise, granular control over how client applications authenticate and are authorized to access event broker services and manage them.
Client applications fall into two categories: messaging apps that connect to event broker services to exchange data and events (e.g., publish/subscribe) and applications that manage and monitor event broker services. These applications helped me to automate the management of event broker services (configuration, monitoring, and so on) that are common in continuous integration and development (CI/CD) workflows.
Authorization and Authentication of Users
To construct event broker services, monitor event broker services, and develop an event-driven architecture, users must be authenticated and authorized. I find this to be a great security measure.
Now, I can effectively manage user accounts and grant permissions so that users can access the various service categories in the Solace Cloud Console using the account and user administration system for Solace Cloud.
Solace Cloud can be coupled with an OpenID Connected central identity management system (SSO) for simpler user management and Single Sign-On. Azure Active Directory, Okta, PingOne, and Auth0 are all supported. I’m surprised at how simple yet secure it is!
Protecting Customer Data
In Solace Cloud, customer data is always safeguarded.
The data is logically divided into a control plane and a message plane by the Solace Cloud architecture. The messaging plane carries the messaging data between the event broker services and client applications, while the control plane carries data for management and monitoring.
The data transfer is encrypted both in transit and at rest using AES-256 and TLS 1.2 on these separate planes, which are quite safe. For the following reasons, the various forms of data are crucial to the security architecture:
- It enabled me to have more control over the data since I could, for example, store all messaging data in a separate VPC or VNet for customer-controlled environments.
- Greater security and reliability (When one plane is hit, the other is unaffected).
System Logs and Audit Logs
Full logs and system notifications are accessible using Solace Cloud, and they include:
- Audit records for access related to security for the Solace Cloud Console.
- Complete logs for the services of the event broker (I access these by setting up SysLog Forwarding)
- Event broker services provide a portion of their logs to the central monitoring server, which is accessible from Solace Insights and helps to generate additional notifications and alerts.
Keep in mind that logs and any other data gathered to check on the status of the system and the event broker services do not include any personally identifying information. And this has made me feel immensely secure!
Industry Standards Adherence
Cloud Security Alliance Consensus Assessments Initiative Questionnaire (CAIQ) v3.1, Service Organization Control (SOC) 2 Type 2, and ISO/IEC 27001:2022 accreditation are only a few of the significant industry standards for cloud and SaaS that Solace Cloud complies with.
Reinforced Operational and Developmental Processes
Security seems to be the priority in the design of Solace Cloud. I find that the security of Solace Cloud is retained due to exceptionally strong developer and operational procedures. The areas consist of:
- Operational practices guaranteeing the security of Solace Cloud production settings and tracking and resolving operational/security incidents with a detailed root-cause investigation.
- Ongoing inspection: Development and production processes make sure that every change is regularly examined with increasing thoroughness. The agile method’s primary focus on security involves threat-modelling analyses and targeted responses to any potential security issues that might be brought up.
- Access Restrictions: With a clear hierarchical access structure and established line of command, I could see that Solace has numerous regulations and stringent internal access restrictions. At every stage of the development and production pipelines, internal audits and testing are routinely conducted to look for vulnerabilities. Ongoing security efforts aim to maintain a safe and dependable environment that continuously improves to fulfill ongoing security requirements.
- HA/DR: The Solace Home Cloud and Solace Cloud Console have 99.95% availability and disaster-recovery plans in place. Numerous safeguards are in place to prevent the loss of important data and to cut down on downtime and recovery time.
- Best Cloud Providers: In order to defend against threats, physical and environmental security uses the top cloud service providers. Vendors are chosen based on necessary controls (such as power/electrical controls, physical-access safeguards, and fire detection/suppression systems).
Additional Security Considerations
The event broker services were installed with a secure configuration, and Solace Cloud is secure by default. I configured further settings to strengthen security and security updates as required.
The initial integration of Solace Cloud’s default settings strikes a balance between security and ease of development and production requirements. When I needed more security, some extra suggestions for my environment were suggested to further harden deployments in the infrastructure I control.
Conclusion
Security is crucial for maintaining the integrity of the services as the event broker services convey the messaging data. Initially, I was a little reluctant. But with understanding and support from the team, I think I eased out. As I started using it, I found Solace Solace Cloud to be a perfect combination of software components and physical sites. My data is secure and private to Solace.
As Solace Cloud adheres to the General Data Protection Regulation (GDPR), which requires Solace to safeguard the personal information and privacy of EU residents, specifically for customers based in the EU, I could trust it completely with my data. Without the express consent of the consumer, personal data will not be used for reasons unrelated to those for which they were obtained; which is so relieving! Solace Cloud is built to enable mission-critical applications and they’ve incorporated enterprise-grade security into every level of the platform to keep our message data safe. Their cutting-edge security safeguards our data so that we can concentrate on creating world-class apps.
I hope this article has helped you understand Solace Cloud’s security capabilities so you can more effectively keep your own deployments safe and secure!
Explore other posts from categories: For Developers | Products & Technology | Solace Scholars

 Solace Scholars
Solace Scholars